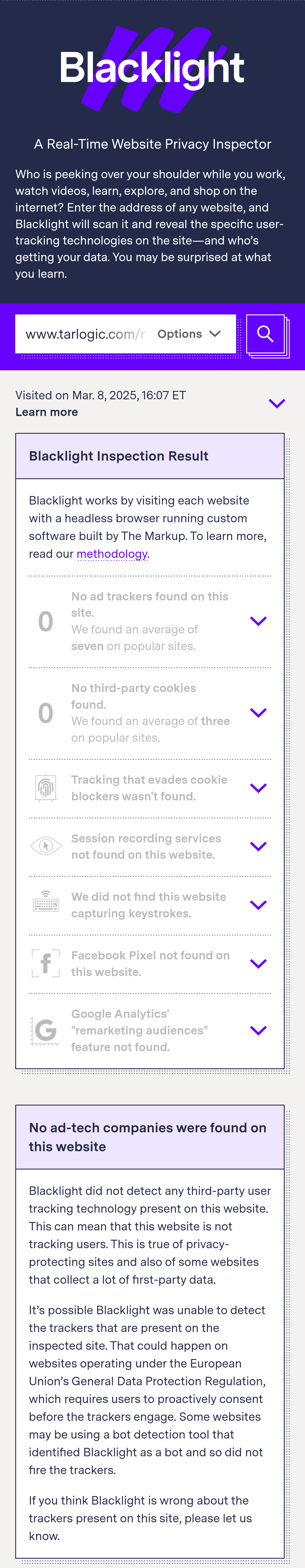
Source Link Privacy.
Tarlogic Security has detected a backdoor in the ESP32, a microcontroller that enables WiFi and Bluetooth connection and is present in millions of mass-market IoT devices. Exploitation of this backdoor would allow hostile actors to conduct impersonation attacks and permanently infect sensitive devices such as mobile phones, computers, smart locks or medical equipment by bypassing code audit controls.
Update: The ESP32 “backdoor” that wasn’t.


The rebuttal wasn’t as comforting as some are making it out to be. They seem to be more interested in the semantics of it not being a backdoor tied to a specific product, which appears to be true.
Rather it is a potential for vulnerability that exists in all wireless implementation, which seems to me to be a bigger issue.
It’s a vulnerability where an attacker already needs code execution on the device/physical access.
If you have that you’re already compromised no matter what.
The biggest risk would be IoT devices.
That’s just the summary of the entire existence of IoT devices
The issue is where the undocumented commands are. They aren’t just allowing any old external person to send payloads to this.
It’s kind of like noticing that someone unexpectedly hid a spare key next to the door… On the inside of the house. Like, sure, maybe the owner would have like to know about that key, but since you have to be inside the house to get to it, it doesn’t really make a difference.
I was reading someone else’s explanation and they said it’s the equivalent of every computer possibly having a backdoor because there is code in a computer that a bad actor can use. There are extra commands that could possibly be used for a backdoor if a malicious actor found a way to use those bits of code. It’s much less oh here is a security vulnerability that is being used and more of a if a robber breaks into our house which is possible they will rob us situation.